1. What is a Hypervisor?
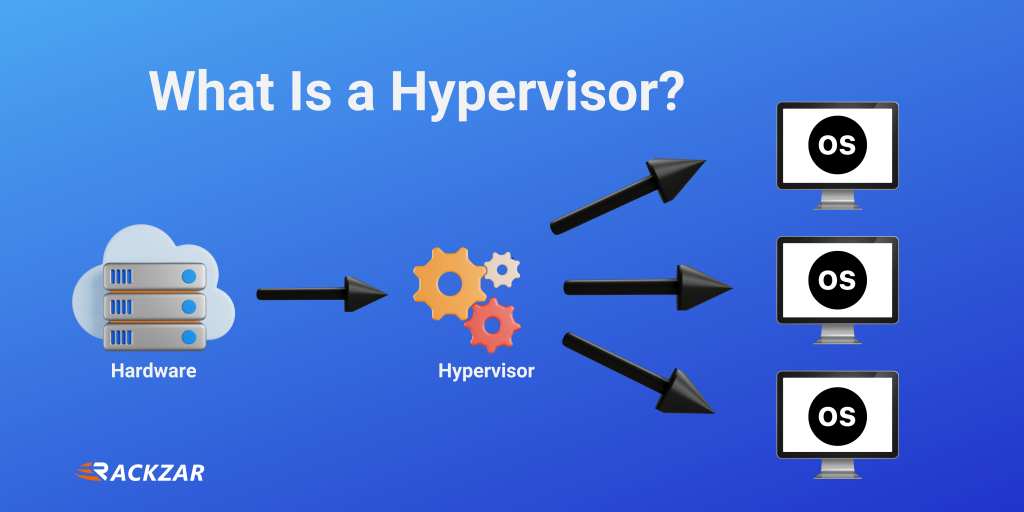
Virtualization has become a fundamental technology in modern computing, allowing for efficient resource utilisation and flexible management of IT infrastructure. The hypervisor is at the heart of virtualization, playing a crucial role in managing virtual machines (VMs) and ensuring the smooth operation of diverse workloads. This comprehensive blog post will explore the world of hypervisors, including their types, functions, and security implications.
2. Understanding Hypervisors
A hypervisor, also known as a Virtual Machine Monitor (VMM), is an entity that either exists in software or hardware form and is used for creating as well as managing virtual machines. Virtualization is a concept that involves abstracting physical hardware resources, such as the CPU, memory, storage, and networking, and then presenting them to multiple VMs. Each VM runs its own operating system (OS). Hypervisors make this abstraction possible by mediating access to physical resources and ensuring the isolation and efficient utilisation of these resources among VMs.
3.Types of Hypervisors
Hypervisors are broadly categorised into two main types: Type 1 (bare-metal) and Type 2 (hosted).

3.1 Type 1 Hypervisors (Bare-Metal)
- Installed directly on the physical hardware.
- Provides high performance and efficiency.
- Examples include VMware ESXi, Microsoft Hyper-V Server, and Xen.
3.2 Type 2 Hypervisors (Hosted)
- Installed on top of a host operating system.
- Suitable for development and testing environments.
- Examples include VMware Workstation, Oracle VirtualBox, and Microsoft Hyper-V (when installed on a Windows OS).
4. What Does a Hypervisor Do?
The primary functions of a hypervisor can be summarised as follows:
4.1 Resource Virtualization
- Abstracts and partitions physical resources, enabling multiple VMs to share them.
- Manages CPU, memory, storage, and networking resources to ensure optimal utilisation
4.2 Isolation:
- Ensures that each VM operates independently of others, preventing interference and conflicts.
- Provides a secure environment for running multiple operating systems on a single physical machine.
4.3 Hardware Abstraction:
- Presents a virtualized view of hardware to VMs, allowing them to run different OS types on the same physical infrastructure.
4.4 Dynamic Resource Allocation:
- Adjusts resource allocation in real-time based on the changing needs of VMs.
- Enhances scalability and responsiveness to workload fluctuations.
4.5 Are Hypervisors Secure?
The security of hypervisors is a critical consideration, given their role in managing multiple VMs and potentially hosting diverse workloads. Here are key aspects to consider
4.6 Hypervisor Security Measures
- Hypervisors employ various security measures to ensure the integrity and isolation of VMs.
- Security features may include secure boot, memory protection mechanisms, and access controls.
4.7 Hypervisor Vulnerabilities
- Like any software, hypervisors may have vulnerabilities that could be exploited by malicious actors.
- Regular updates and patches are crucial to addressing and mitigating potential security risks.
4.8 Guest VM Isolation:
- Ensures that vulnerabilities or compromises in one VM do not affect the security of other VMs on the same hypervisor.
4.9 Security Best Practices:
- Following best practices, such as minimising the attack surface, implementing proper access controls, and regular security audits, enhances hypervisor security.
Conclusion
To sum up, hypervisors have a crucial role in the virtualization landscape. They allow organisations to optimise resource utilisation and simplify IT management. It is important to have knowledge about the different types and functions of hypervisors to make informed decisions about virtualized infrastructure. Although hypervisors are designed with security in mind, it is crucial for organisations to follow best practices and stay alert to mitigate potential risks and ensure a secure virtualization environment.







